This section provides solutions for common issues you might encounter.
Where to find OAK in documentation
OAK is the key required for authorization when a camera (or any other Axis network device) is registered and connected to the system via the Axis O3C/AVHS service.
The OAK can be found printed on the documentation included in the camera package.

If you do not have a printed OAK, you can obtain it from the camera interface.
Where to find OAK in the camera interface
NOTICE
This feature is available on the camera from firmware versions 5.51.7, 6.50.5.2, 8.40.4, 9.80.2 or 10.0.0.
Log in to the camera’s user interface as an administrator. Make sure the camera has a FW that has this feature (see above).
The paths to display the OAK key are then different for each version:
- Firmware based on 5.51: go to Setup → System options → Support → System Overview.
- Firmware based on 6.50: go to Setup → System options → Support → System Overview.
- Firmware based on 8.40: go to System → AVHS, then click Retrieve OAK.
- Firmware based on 9.80: go to System → AVHS, then click Retrieve OAK.
- Firmware based on 10.0 or higher: go to System → O3C, then click Retrieve OAK.
Re-connecting a camera that has been reset to factory settings
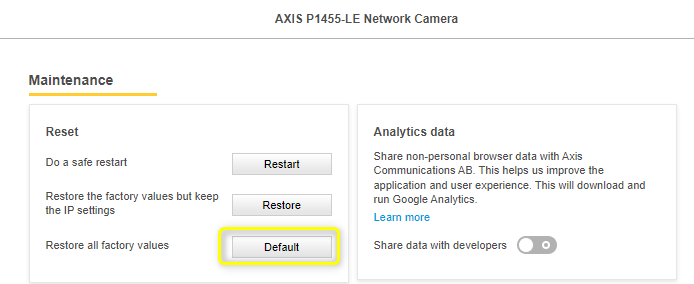
If you reset the camera to factory settings using the Default button on the camera interface or the HW button on the camera body, the camera will be disconnected from the servers. However, the camera remains registered in the system.
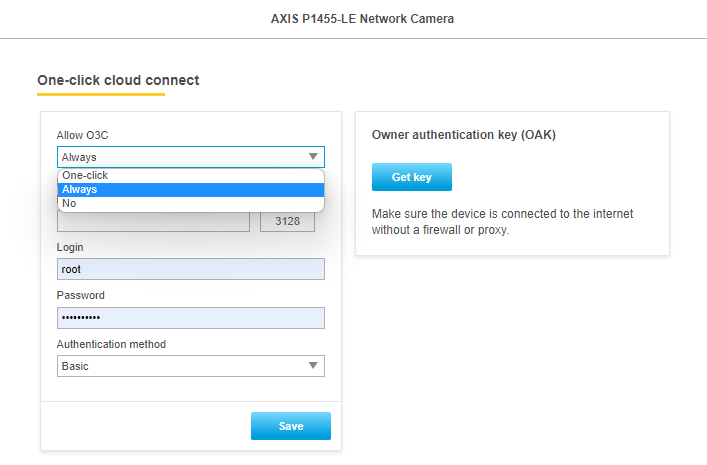
To reconnect the camera, you need to enable the O3C function on the camera, also called AVHS in older versions of FW. There are several ways to enable this function.
- Press the button on the camera body to enable the O3C/AVHS function.
- Suitable when the camera is physically very easy to access or when you are unable to access the camera’s user interface.
- Set this function in the camera user interface (Settings > System > O3C/AVHS).
- Easiest way if you are connected on the same network as the camera.
- By installing and opening the Camera Connector application.
- The Camera Connector application is useful if the camera connection fails in the previous ways. It has some basic diagnostic functions that can tell you where the problem is. Again, however, you need the ability to access the camera’s user interface.
HINT
If you need to reset the camera to factory settings but do not want it to disconnect, use the Restore button instead of the Default button. This will preserve the TCP/IP parameter settings and O3C/AVHS settings.
Credit card can’t be verified
In order to verify and prove authenticity of the credit card, an $0 or $1 charge will be implemeted and only upon succesful authorisation will the credit card then be considered as acceptable, for future subsequent service payments.
The charged amount will then be refunded back to the card.
If the attempt to charge and add the card is not successful, proceed as follows:
- Try adding another credit card.
- Check that the card is not blocked and that it has internet payments enabled. This can be checked via your online banking or contact your bank for assistance
- Contact your bank and ask for verification of the failed payment. If the bank resolves the issue, retry the charge attempt.
- If the above steps did not resolve the issue, contact our helpdesk.
Web Application Firewall
In the realm of cloud-based video surveillance, ensuring the highest levels of security is paramount. As digital technologies advance, so do the threats to web applications. In response to these challenges, Web Application Firewalls (WAFs) have emerged as crucial components in safeguarding web applications. One such powerful WAF is ModSecurity, which can play a pivotal role in enhancing the security of cloud-based web services.
Unveiling ModSecurity
ModSecurity stands as an open-source, cross-platform web application firewall, designed to serve as a robust security shield for web applications. Originally developed by Trustwave’s SpiderLabs, ModSecurity is tailored to protect web applications from an extensive range of threats, including but not limited to SQL injection, cross-site scripting (XSS), remote file inclusion, and other malicious attacks.
Elevating Security with ModSecurity
Utilizing ModSecurity in a cloud-based video surveillance application offers a multitude of benefits, ensuring a robust security posture.
- Reliable protection supported by OWASP: ModSecurity provides comprehensive protection against the top ten web application security risks identified by the Open Web Application Security Project (OWASP). To bolster this defense, our ModSecurity configuration is based on the Core Rule Set (CRS) maintained by OWASP. By doing so we ensure the system remains fortified against prevalent attacks, in alignment with industry best practices and the latest threat intelligence.
- Real-Time Threat Detection: ModSecurity employs a rule-based approach to promptly identify and thwart malicious traffic in real-time. By analyzing incoming HTTP requests and responses, it can detect and mitigate attacks as they occur, preserving the integrity and security of valuable data.
- Tailored Rule Set: The ModSecurity rule set in operation is customized to align with the specific security requirements of our system. This flexibility allows ModSecurity to adapt and provide targeted protection, addressing unique attack patterns within the context of cloud-based video surveillance.
- Robust Logging and Monitoring: ModSecurity generates comprehensive logs of all incoming requests and blocked attacks. These logs facilitate the tracking and analysis of security incidents, empowering proactive threat mitigation. Vigilant monitoring is especially critical for safeguarding sensitive data accumulated by our system.
- Versatile Integration: ModSecurity is not confined to a single web server or application framework. It seamlessly integrates with popular web servers like Apache and Nginx, as well as various programming languages and content delivery systems, ensuring compatibility with diverse cloud-based infrastructure.
- Active Open-Source Community: Being an open-source solution, ModSecurity benefits from a vibrant community of developers and users. This active community continually enhances the firewall’s engine capabilities, keeping it up-to-date with emerging requirements to contemporary software of this kind.
How ModSecurity Works with the System
ModSecurity operates as a web server’s module, integrated into the web application’s infrastructure. Upon receiving incoming HTTP requests, ModSecurity evaluates them against predefined and custom rule sets, carefully tailored to our specific use cases. If it identifies suspicious activity or matches known attack patterns, it takes appropriate actions, such as blocking data exchange with the web application, logging event and alerting administrators. This proactive defense mechanism ensures the security of our service.